In this blog post, we will discuss Phishing and give you tips and advice on how to protect your important data from such attacks.
What is Phishing?
Phishing is a type of social engineering or cyber-attack that uses fake emails, websites, calls, and messages to trick people into providing sensitive information or downloading malicious software.
How Does Phishing Work?
Phishing works by sending messages that appear to be from someone or a service you know or trust, such as a bank, government agency, or business.
The message can contain a link to a malicious or fake website that will prompt the user to enter valuable personal information. This may include login credentials (your username and password), financial information, as well as other personal data such as a PPS number. This information can then be used to commit crimes such as theft from your bank account.
Phishing emails may also contain an attachment that when downloaded will install malicious software onto your device. Once installed, this 'Malware' will allow the attacker to access your device enabling them to steal data.
Phishing attacks range in sophistication from 'spam' messages that are not targeted to tailor-made messages designed specifically for the recipient.
The Dangers of Phishing
Phishing attacks can have grave consequences. Personal and financial data can be stolen which in turn can be used for identity theft or financial fraud.
Phishing can also lead to the installation of malware on a computer, which can be used to monitor activities and steal data. In addition, being subject to a successful phishing attack may also damage a company's or institution’s reputation.
Types of Phishing Attacks
There are many types of phishing attacks, each with its own unique characteristics. Phishing attacks include:
- Spear phishing: This type of attack targets specific individuals or companies. The attacker will send a highly personalised email that appears to be from a trusted source.
- Whaling: Whaling attacks target high-level executives, such as CEOs and CFOs. The attacker will impersonate a legitimate source to get access to sensitive information.
- Business email compromise (BEC): This type of attack targets businesses by sending emails that appear to be from a trusted source, such as a supplier or customer. The attacker will then attempt to get the business to transfer money or provide sensitive information.
- Vishing: Vishing is a type of phishing attack that uses voice messages to target victims. The attacker will impersonate a company or government agency to get the victim to provide sensitive information.
- Smishing: Smishing is a type of phishing attack that uses text messages to target victims. The attacker will send a text message that appears to be from a legitimate source, such as a bank or government agency, to get the victim to provide sensitive information.
Tips to Protect Yourself from Phishing Attacks
The best way to prevent phishing attacks is to be vigilant and aware of the signs of a phishing attack. Below are some tips to help your data out of the hands of cybercriminals:
- Treat emails from unknown sources with caution. Do not click on links or open attachments in emails from unknown sources.
- Do not respond to emails or texts that request personal or sensitive information.
- If you do receive an email that appears to be from a legitimate source, but you are unsure whether to act upon it, call the company or organisation directly to verify it.
- Use caution with websites that do not have a security certificate (sites that do not contain the prefix https://).
- Use strong passwords and change them regularly.
- Use two-factor authentication when available.
- Use antivirus software and anti-malware software and keep it up to date. In addition, scan your computer for viruses and malware regularly.
- Use anti-phishing software to scan emails for malicious links and attachments.
- Use Advanced Email Threat Protection software to identify and filter out harmful emails.
- Be careful with the information you share on social media as this can be used to build a profile that an attacker can use to create a spear phishing attack.
- Educate yourself! Reading blog posts such as this will certainly help, but dedicated Human Risk Management software will help to educate you and your company.
How to Identify Phishing Emails
Email is the most popular form of Phishing attack. Phishing emails are designed to look legitimate, so it can be difficult to tell if an email is a phishing attack or not.
However, there are tell-tale signs that can help you identify suspicious emails:
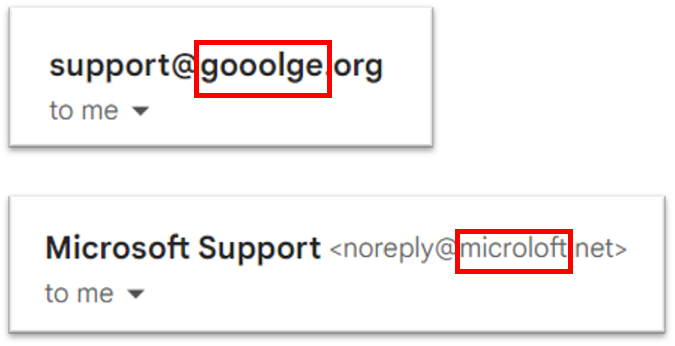
- The sender's email address does not match the company or organisation they are claiming to be from. Here we have two examples purporting to be from Google and Microsoft:
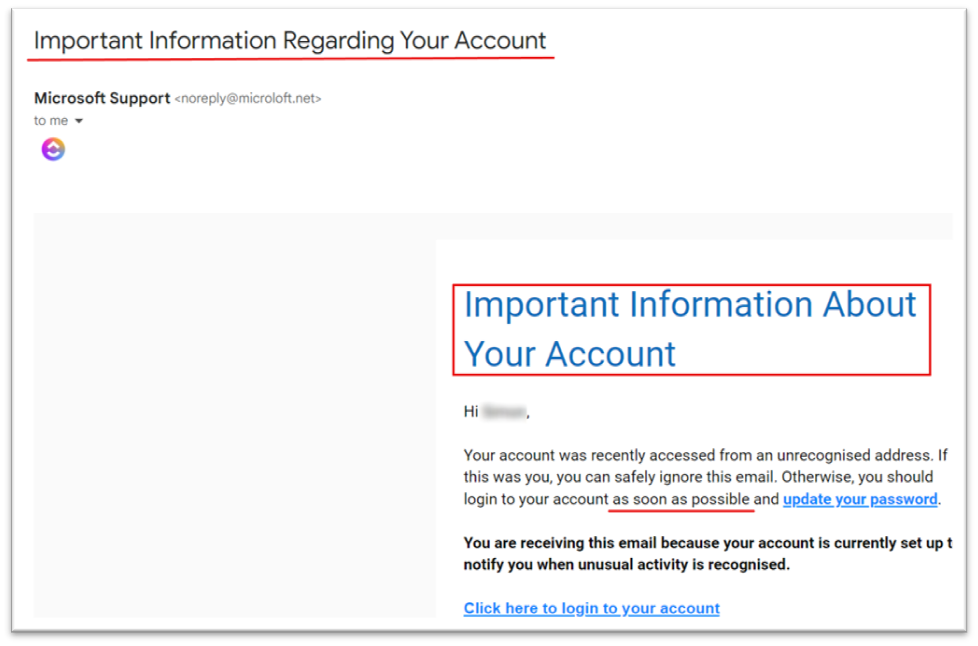
- The email contains threats or pressure to act quickly. We can see this in the sample Phishing email below:
- The email contains spelling or grammatical errors such as this Phishing email claiming to be from the newspaper The Irish Times:

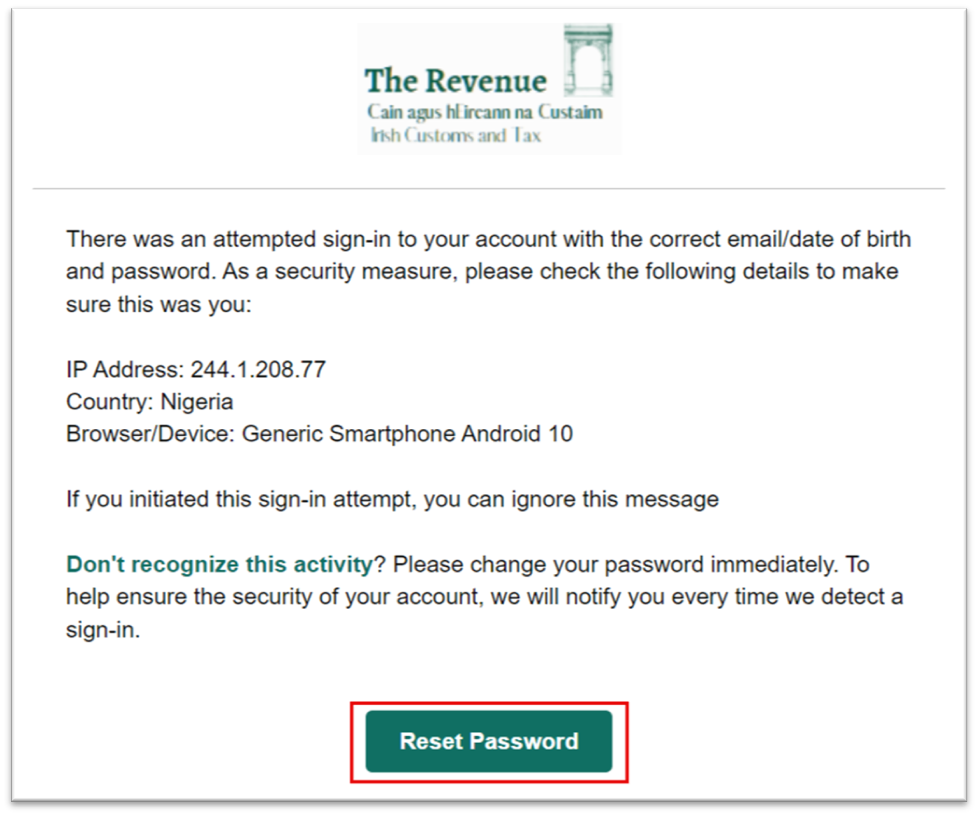
- The email contains suspicious links or attachments. The Phishing email below claims to be from Revenue and contains a link to change your password - at which point you will be taken to a fake website which will then capture your login credentials:
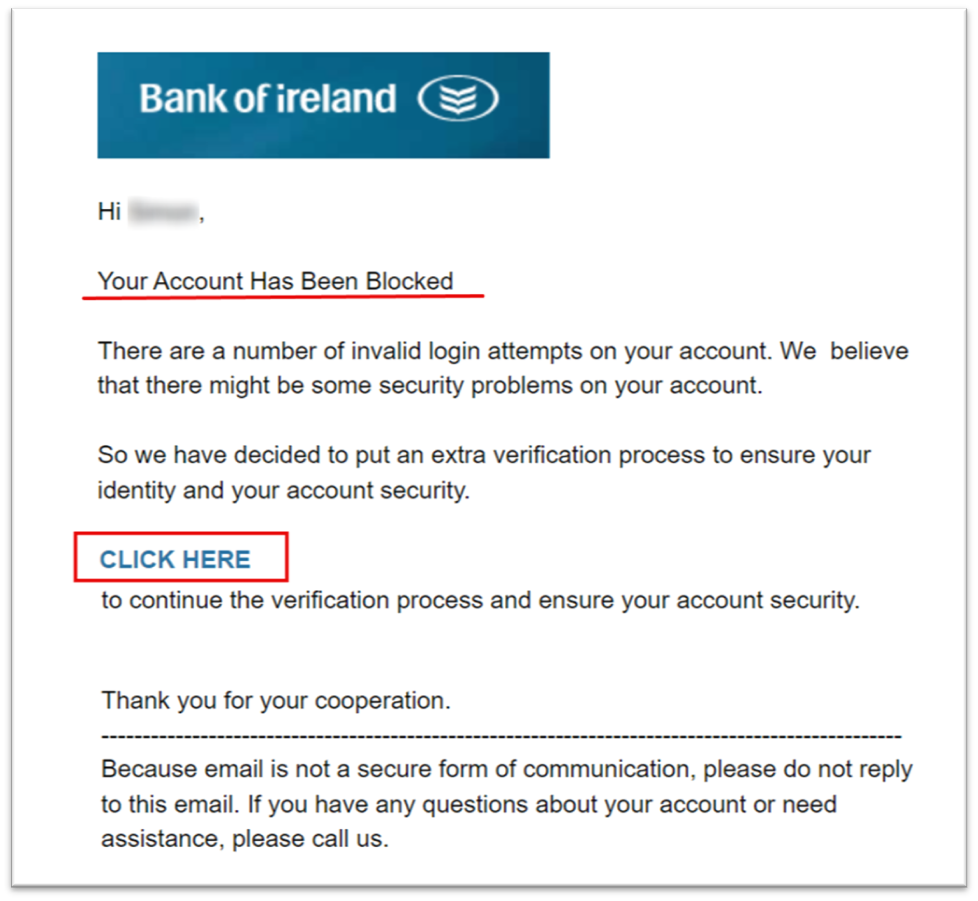
- The email requests personal information, such as login credentials, PPSN, or a credit/debit card number. In the example below, the recipient is being asked to go through a 'verification process' that will involve capturing personal information:
What to Do If You Suspect a Phishing Attack
A good, well-managed antivirus or advanced email protection system will block almost all phishing attacks. But attacks change and sometimes even the best defences will not work. That is where your judgement comes into play.
If you think you have received a phishing email or message, the most important thing to do is not to respond or click on any links or attachments. If you are a business user, report the email to your IT team. If you are a home user, you can contact the 'sender' directly (not using any links or contact information in the suspected Phishing message).
You should also check for any suspicious activity on your accounts or devices and change any passwords that may have been compromised.
Conclusion
Phishing is one of the most common forms of cybercrime and it is important to understand how to protect yourself. By following the tips outlined in this blog post, you can reduce the risk of becoming a victim of a phishing attack.
Remember to always be vigilant and aware of the signs of a phishing attack, and if you think you have received a phishing email or message, do not respond, download, or click on any links!
Frequently Asked Questions
Q: What is phishing?
A: Phishing is a type of cyber-attack that tricks people into providing sensitive information or downloading malicious software.
Q: How can I protect myself from phishing attacks?
A: Be vigilant and aware of the signs of a phishing attack. Don't click on links or open attachments in emails from unknown sources. Use strong passwords, two-factor authentication, and antivirus software. Be careful with the information you share on social media, and educate yourself.
Q: How can I identify phishing emails?
A: Look for signs such as the sender's email address not matching the company or organization they claim to be from, threats or pressure to act quickly, spelling or grammatical errors, suspicious links or attachments, and personal information requests.
Q: What should I do if I suspect a phishing attack?
A: Don't respond or click on any links or attachments. Report the email to your IT team if you're a business user, or contact the 'sender' directly (not using any links or contact information in the suspected Phishing message) if you're a home user. Check for suspicious activity and change any passwords that may have been compromised.

